
| Filename extension | |
|---|---|
| Internet media type | application/x-pkcs12 |
| Uniform Type Identifier (UTI) | 0 |
| Developed by | RSA Security |
| Initial release | 1996 |
| Latest release | |
| Type of format | Archive file format |
| Container for | X.509 public key certificates, X.509 private keys, X.509 CRLs, generic data |
| Extended from | Microsoft PFX file format |
In cryptography, PKCS #12 defines an archive file format for storing many cryptography objects as a single file. It is commonly used to bundle a private key with its X.509 certificate or to bundle all the members of a chain of trust.
A PKCS #12 file may be encrypted and signed. The internal storage containers, called 'SafeBags', may also be encrypted and signed. A few SafeBags are predefined to store certificates, private keys and CRLs. Another SafeBag is provided to store any other data at individual implementer's choice.[1][2]
PKCS #12 is one of the family of standards called Public-Key Cryptography Standards (PKCS) published by RSA Laboratories.
The filename extension for PKCS #12 files is .p12 or .pfx.[3]
These files can be created, parsed and read out with the OpenSSLpkcs12 command.[4]
Description While USM Appliance requires PEM Formatted (ASCII PEM formatted X.509) certificates for uploading to the Appliance, some registrars may only provide certificates in PKCS12 format, which is not compatible. In this scenario, the PKCS12 certficates can be uploaded to the Appliance, and then converted through jailbreak.
- PKCS #12 file that contains a trusted CA chain of certificates. Cat sub-ca.pem root-ca.pem ca-chain.pem openssl pkcs12 -export -in ca-chain.pem -caname sub-ca alias -caname root-ca alias -nokeys -out ca-chain.p12 -passout pass:pkcs12 password PKCS #12 file that contains a user certificate, user private key, and the associated CA certificate.
- PKCS7 gets used a lot of with email certificates and forms the basis for S/MIME secure email. PKCS8 is a similar standard used for carrying private keys. And finally, we have PKCS12, which provides better security via encryption.
Relationship to PFX file format[edit]
PKCS #12 is the successor to Microsoft's 'PFX';[5]however, the terms 'PKCS #12 file' and 'PFX file' are sometimes used interchangeably.[3][4][6]
The PFX format has been criticised for being one of the most complex cryptographic protocols.[6]

Normal usage[edit]

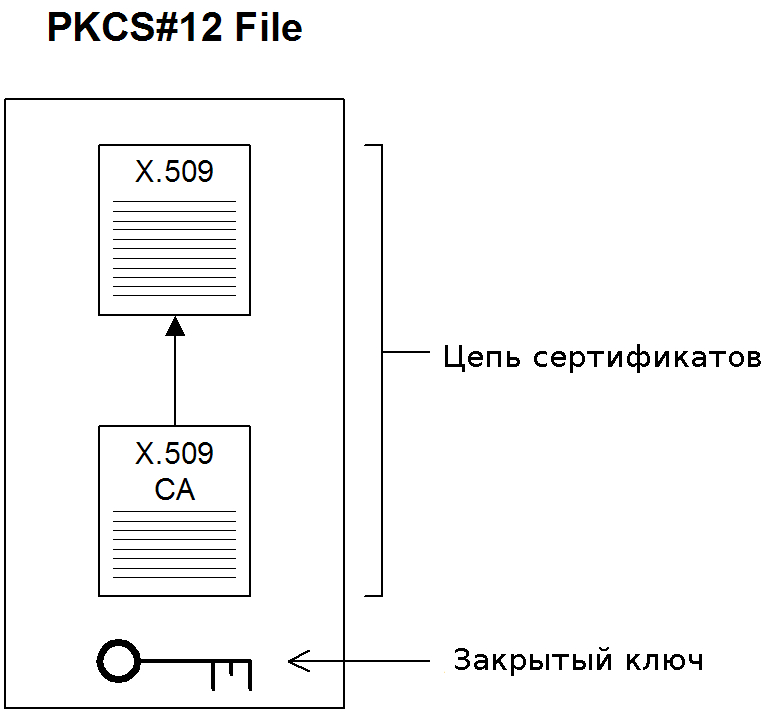
The full PKCS #12 standard is very complex. It enables buckets of complex objects such as PKCS #8 structures, nested deeply. But in practice it is normally used to store just one private key and its associated certificate chain.
PKCS #12 files are usually created using OpenSSL, which only supports a single private key from the command line interface. The Java keytool can be used to create multiple 'entries' since Java 8, but that may be incompatible with many other systems. As of Java 9, PKCS #12 is the default keystore format.[7][8]


A simpler, alternative format to PKCS #12 is PEM which just lists the certificates and possibly private keys as Base 64 strings in a text file.
GnuTLS's certtool may also be used to create PKCS #12 files including certificates, keys, and CA certificates via --to-p12. However, beware that for interchangeability with other software, if the sources are in PEM Base64 text, then --outder should also be used.
References[edit]
- ^'PKCS #12: Personal Information Exchange Syntax Standard'. RSA Laboratories. Archived from the original on 2017-04-17.
This standard specifies a portable format for storing or transporting a user's private keys, certificates, miscellaneous secrets, etc.
- ^'PKCS 12 v1.0: Personal Information Exchange Syntax'(PDF). RSA Laboratories. 1999-06-24. Retrieved 2020-01-16.
- ^ abMichel I. Gallant (March 2004). 'PKCS #12 File Types: Portable Protected Keys in .NET'. Microsoft Corporation. Retrieved 2013-03-14.
All Windows operating systems define the extensions .pfx and .p12 as Personal Information Exchange, or PKCS #12, file types.
CS1 maint: discouraged parameter (link) - ^ ab'openssl-cmds: pkcs12'. OpenSSL Project. 2019. Retrieved 2020-01-16.
The pkcs12 command allows PKCS#12 files (sometimes referred to as PFX files) to be created and parsed.
CS1 maint: discouraged parameter (link) - ^Peter Gutmann (August 2002). 'Lessons Learned in Implementing and Deploying Crypto Software'(PDF). The USENIX Association. Retrieved 2020-01-16.
In 1996 Microsoft introduced a new storage format [...] called PFX (Personal Information Exchange) [...] it was later re-released in a cleaned-up form as PKCS #12
CS1 maint: discouraged parameter (link) - ^ abPeter Gutmann (1998-03-12). 'PFX - How Not to Design a Crypto Protocol/Standard'. Retrieved 2020-01-16.CS1 maint: discouraged parameter (link)
- ^'JEP 229: Create PKCS12 Keystores by Default'. OpenJDK JEPs. Oracle Corporation. 2014-05-30.
- ^Ryan, Vincent (2014-05-30). 'Bug JDK-8044445: Create PKCS12 Keystores by Default'. JDK Bug System.
External links[edit]
- RFC7292 - PKCS #12: Personal Information Exchange Syntax v1.1
- 'PKCS #12: Personal Information Exchange Syntax Standard'. RSA Laboratories. Archived from the original on 2017-04-17.
This standard specifies a portable format for storing or transporting a user's private keys, certificates, miscellaneous secrets, etc.
- Overview about PKCS#12 capabilities, usage, implementations, history and future: Ryan Hurst and Yury Strozhevsky (2015-12-02). 'The PKCS#12 standard needs another update'. Archived from the original on 2017-03-03.
Generate an LDAP client certificate for mutual authentication using OpenSSL. The final output is a PKCS#12 certificate stored within a Java keystore.
About this task
See the OpenSSL documentation for more information about generating certificates. These steps assume you have access to OpenSSL.
Enter these commands in a command line interface.
- Generate a self-signed client certificate. For example, this command creates a client certificate test1-cert.crt based on the test1-key.key private key.
- Convert both the certificate file and private key to PKCS#12 (a file with a .pfx or .p12 extension). For example, this command converts the client certificate and private key to a PKCS#12 certificate called test1-certificate.pfx.
- Generate the Java Key Store and import the pkcs12 file into it. For example, this command imports the certificate to the test1.jks Java keystore.
- Upload the certificate in the keystore file (
test1.jks) to the instance.
Pfx Format
What to do next
Pkcs12 Certificate File Extension
Upload a certificate to an instance